How secure you ci/cd pipeline?
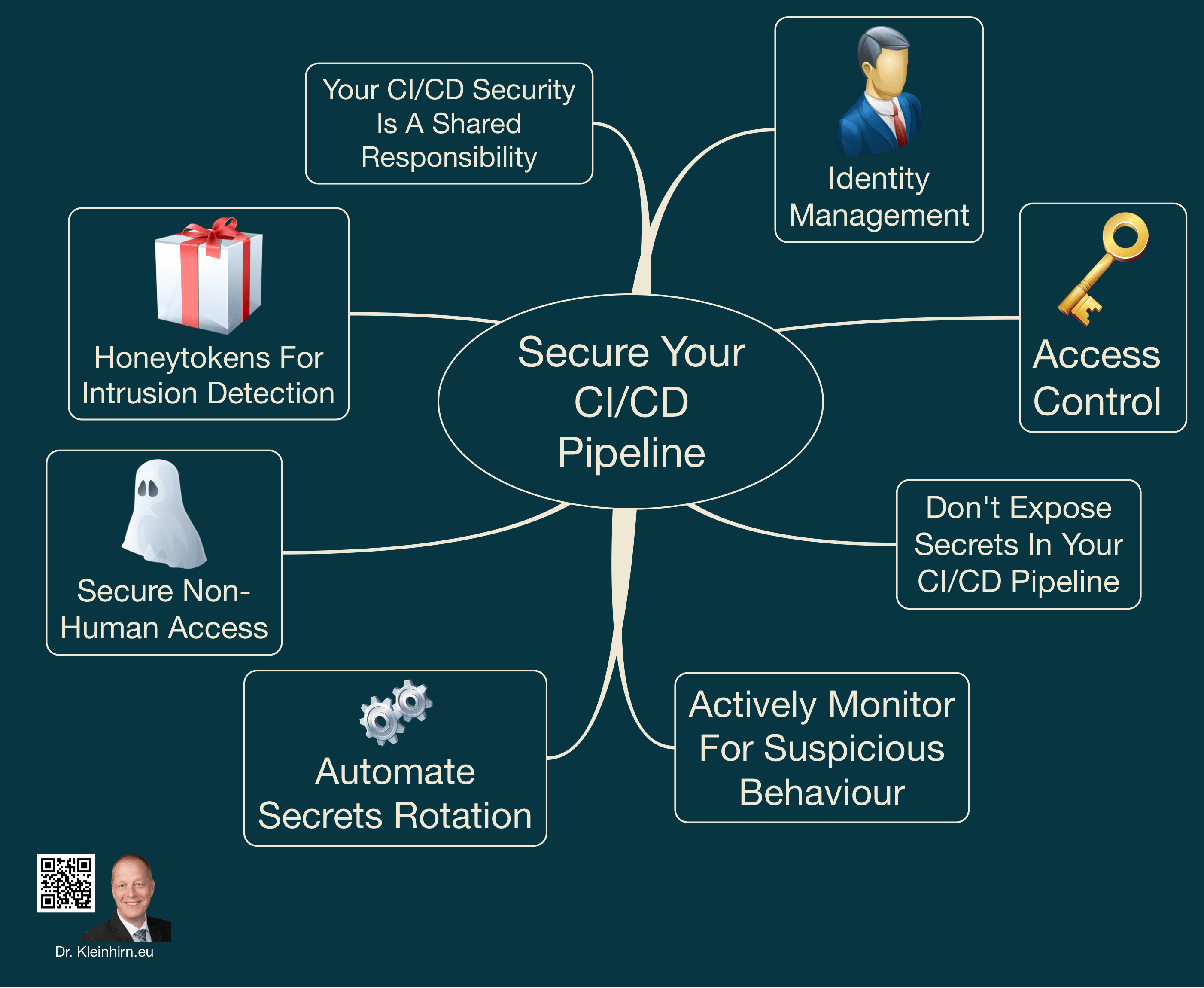
Securing your CI/CD (Continuous Integration/Continuous Deployment) pipeline is crucial to ensuring the integrity and safety of your software development process. Here are a few best practices to follow:
Use a private repository for your code: This will ensure that only authorized individuals have access to your source code.
Implement access controls: Use tools such as GitHub or GitLab to control who has access to your repository and what actions they can perform.
Use secure authentication: Utilize multi-factor authentication for all users to prevent unauthorized access.
Use a secure connection: Use HTTPS or SSH to ensure that all communication between the pipeline and the repository is secure.
Keep your dependencies updated: Use a dependency manager to ensure that all dependencies are up to date and free from known vulnerabilities.
Regularly perform security scans: Use tools such as OWASP ZAP or Nessus to regularly scan your pipeline for vulnerabilities.
Have a disaster recovery plan: Have a plan in place to quickly and effectively respond to any security breaches that may occur.
By following these best practices, you can ensure that your CI/CD pipeline is secure and that your software development process is protected from potential threats.
Download secure-ci-cd-pipeline.pdf.