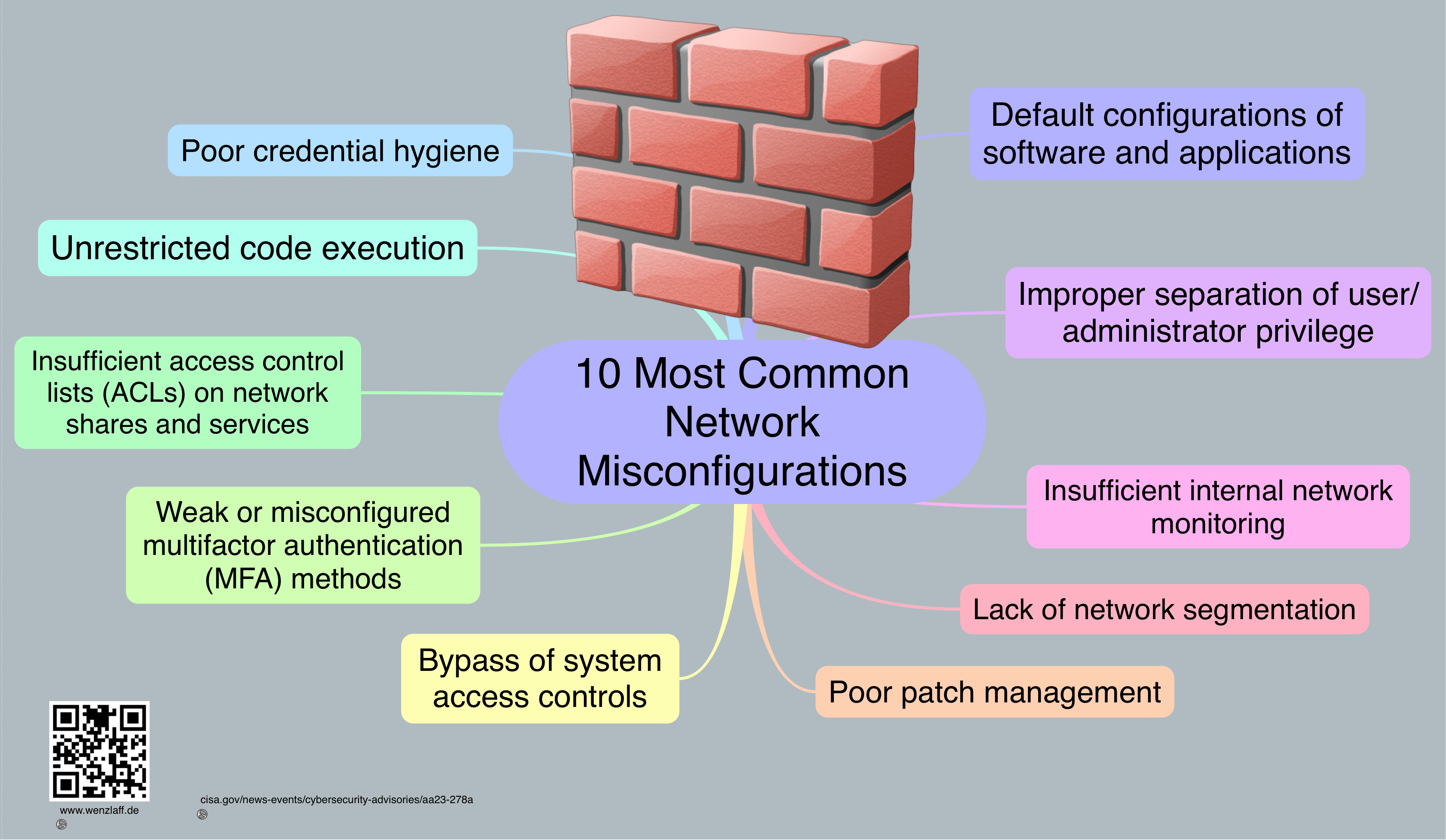
Certainly, here are 10 common network and software/application misconfigurations and security issues:
Default Configurations of Software and Applications:
– Many software and applications come with default settings that may not be secure. Failing to change these defaults can leave systems vulnerable. It’s crucial to review and configure software and applications according to security best practices.
Improper Separation of User/Administrator Privilege:
– Granting users unnecessary administrative privileges can result in security breaches. Ensure that users only have the permissions they need to perform their tasks, and use the principle of least privilege to restrict access.
Insufficient Internal Network Monitoring:
– Focusing solely on external threats can lead to missed internal threats. Implement internal network monitoring to detect unusual or suspicious activities within your network.
Lack of Network Segmentation:
– Without proper network segmentation, a breach in one part of the network can lead to unauthorized access to other segments. Implement segmentation to isolate critical assets and limit lateral movement in the event of a breach.
Poor Patch Management:
– Delayed or neglected patch management can expose systems to known vulnerabilities. Establish a robust patch management process to promptly apply security updates and patches to all systems and applications.
Bypass of System Access Controls:
– Inadequate controls on system access can lead to unauthorized access. Regularly review and update access controls, ensuring they align with your organization’s security policies.
Weak or Misconfigured Multifactor Authentication (MFA) Methods:
– Weak MFA methods or improper configurations can be exploited by attackers. Implement strong MFA mechanisms and regularly review their effectiveness to enhance authentication security.
Insufficient Access Control Lists (ACLs) on Network Shares and Services:
– Misconfigured ACLs can result in unauthorized access to sensitive data. Regularly audit and adjust ACLs to restrict access to only authorized users and services.
Poor Credential Hygiene:
– Inadequate password policies, such as weak or easily guessable passwords, can lead to account compromises. Enforce strong password policies and encourage users to regularly update their credentials.
Unrestricted Code Execution:
– Allowing untrusted code to execute can lead to vulnerabilities and exploits. Employ code reviews, application sandboxing, and robust security testing to prevent uncontrolled code execution.
To mitigate these common misconfigurations and security issues, organizations should establish comprehensive security policies, conduct regular security assessments and audits, provide training to staff on security best practices, and implement automated security controls wherever possible. Regularly monitoring and adapting to emerging threats is also essential to maintaining a secure network and software environment.
Download network-misconfigurations.pdf.